August 30, 2025
Keeping accounts safe is core to EZ-QDAi. Our custom email/password flow combines client-side hashing, strong server-side hashing, and a staged activation process to protect credentials end-to-end.
1) Client-side SHA-256: Never Send Raw Passwords Over The Wire
When users log in (e.g., first-time login using a temporary password), the browser hashes the entered password with SHA-256 before sending it to the server. This provides an extra layer of protection beyond HTTPS by ensuring the raw password is never transmitted in plaintext.
- Password → SHA-256 in the browser
- Server receives only the hex-encoded hash
- HTTPS still required and enforced for transport security
2) Server-side bcrypt with Per-User Salt
On the backend, EZ-QDAi uses bcrypt to securely store passwords. Bcrypt is a slow, memory-hard password hashing function designed to resist brute-force attacks.
- Each password is hashed with a unique per-user salt
- Cost factor is tuned to $2b$12$ (work factor 12) for strong security on modern hardware
- Stored values look like: $2b$12$<22-char-salt><31-char-hash>
3) Staged Activation with Temporary Passwords
New signups receive a time-bound activation link and a temporary password is generated upon activation. Users must log in with that temporary password and immediately change it.
- Activation token: single-use, expires after a short window
- Temporary password: valid only until first successful change
- Mandatory password change: enforces creation of a long-term secret known only to the user
4) Defense-in-Depth Summary
- HTTPS protects in-transit data
- Client-side SHA-256 avoids transmitting raw passwords
- Server-side bcrypt + salt defends at-rest credentials
- Activation + temp password eliminates account bootstrapping risks
- Staging gates prevent sensitive testing tools from leaking into production
Tips for Strong Passwords:
- Use 12+ characters
- Mix upper/lowercase, numbers, and symbols
- Avoid reused passwords
- Consider a password manager
With these practices and our layered design, EZ-QDAi provides robust, modern protection for your account.
 Joebert Jacaba
Joebert Jacaba
July 16, 2025 23:15
In today's increasingly complex digital landscape, network security has become paramount for businesses of all sizes. Omada Network Security solutions provide enterprise-grade protection that scales with your organization's needs, offering comprehensive security features without the enterprise price tag.
Key Features of Omada Network Security:
- Advanced threat detection and prevention
- Centralized management and monitoring
- Scalable architecture for growing businesses
- Integration with existing network infrastructure
- Real-time security analytics and reporting
- GDPR-compliant security frameworks
As an AI-driven technology consultant serving European businesses, we understand the importance of intelligent security solutions that can adapt to evolving threats while maintaining compliance with EU regulations. Omada's approach to network security aligns perfectly with our philosophy of delivering enterprise-grade technology solutions that are accessible and affordable for businesses at every stage of growth.
 Joebert Jacaba
Joebert Jacaba
July 16, 2025 22:37
In just a few focused hours, we completely transformed our website using Cursor AI as our development partner. What would have taken weeks of traditional development was accomplished in hours, demonstrating the power of AI-assisted coding for rapid business transformation in the European market.
Key Achievements:
- Migrated from Python to Rust for email functionality, improving performance and security
- Implemented GDPR-compliant cookie consent with minimal JavaScript
- Enhanced mobile responsiveness with proper dropdown navigation
- Refined AI-driven messaging while maintaining traditional IT outsourcing capabilities
- Fixed broken links and improved overall site navigation
- Optimized logo sizing and header layout for better user experience
The collaboration with Cursor AI showcased how modern development tools can accelerate business transformation for European companies. Every change was implemented with precision, from backend Rust integration to frontend UX improvements, all while maintaining our commitment to being an AI-driven company that delivers both cutting-edge AI solutions and reliable traditional IT services.
 Joebert Jacaba
Joebert Jacaba
November 5, 2018 06:56
We are sharing with the European open source community the Nagios Plugins we have written for Kubernetes which focus on Prometheus. We moved some projects to GitLab after Microsoft acquired GitHub, valuing GitLab's support for free private repositories for sensitive projects. Today, both platforms offer strong open source and privacy features that align with European data protection standards.
Please click on the title to take you to the Gitlab repository.
 Joebert Jacaba
Joebert Jacaba
August 26, 2018 16:08
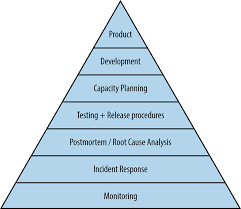
Monitoring is the foundation of Service Reliability. You will only know there is a problem when users complain. The objective of monitoring is to detect problems before users notice them. This way you will have time for decision-making on how to address the impending incident.
 Joebert Jacaba
Joebert Jacaba
August 26, 2018 15:53
The owner of one of the largest banks in Europe once said that his company is a technology company with financial-domain expertise. The board laughed at him in secret. Today, his bank is leading in embracing technology, proving that his vision is essential for companies to survive in the European market.
 Joebert Jacaba
Joebert Jacaba
August 15, 2018 10:30
As we move towards a more containerized and microservices-based architecture, the importance of cloud-native development practices becomes increasingly clear. Kubernetes has emerged as the de facto standard for container orchestration, and with it comes a new paradigm for application development and deployment that European businesses must embrace.
In this article, we explore the key principles of cloud-native development and how European organizations can successfully transition to this modern approach while maintaining compliance with EU regulations.
 Joebert Jacaba
Joebert Jacaba
August 10, 2018 14:22
As artificial intelligence becomes more prevalent in European business applications, ensuring GDPR compliance becomes increasingly important. This article explores the key considerations for implementing AI solutions while maintaining full compliance with European data protection regulations.
 Joebert Jacaba
Joebert Jacaba
July 25, 2018 09:15
The European business landscape presents unique challenges and opportunities for digital transformation. From regulatory compliance to cultural considerations, European companies must navigate a complex environment while embracing modern technology solutions.
 Joebert Jacaba
Joebert Jacaba
 Joebert Jacaba
Joebert Jacaba